Welcome To Investigating Windows ‘writeup’
-
by : Ahmedhammad
–info
- room name : Investigating Windows
- category : Windows Forensics
- This is a challenge that is exactly what is says on the tin, there are a few challenges around investigating a windows machine that has been previously compromised.
Starting Point
Task 1 : Investigating Windows
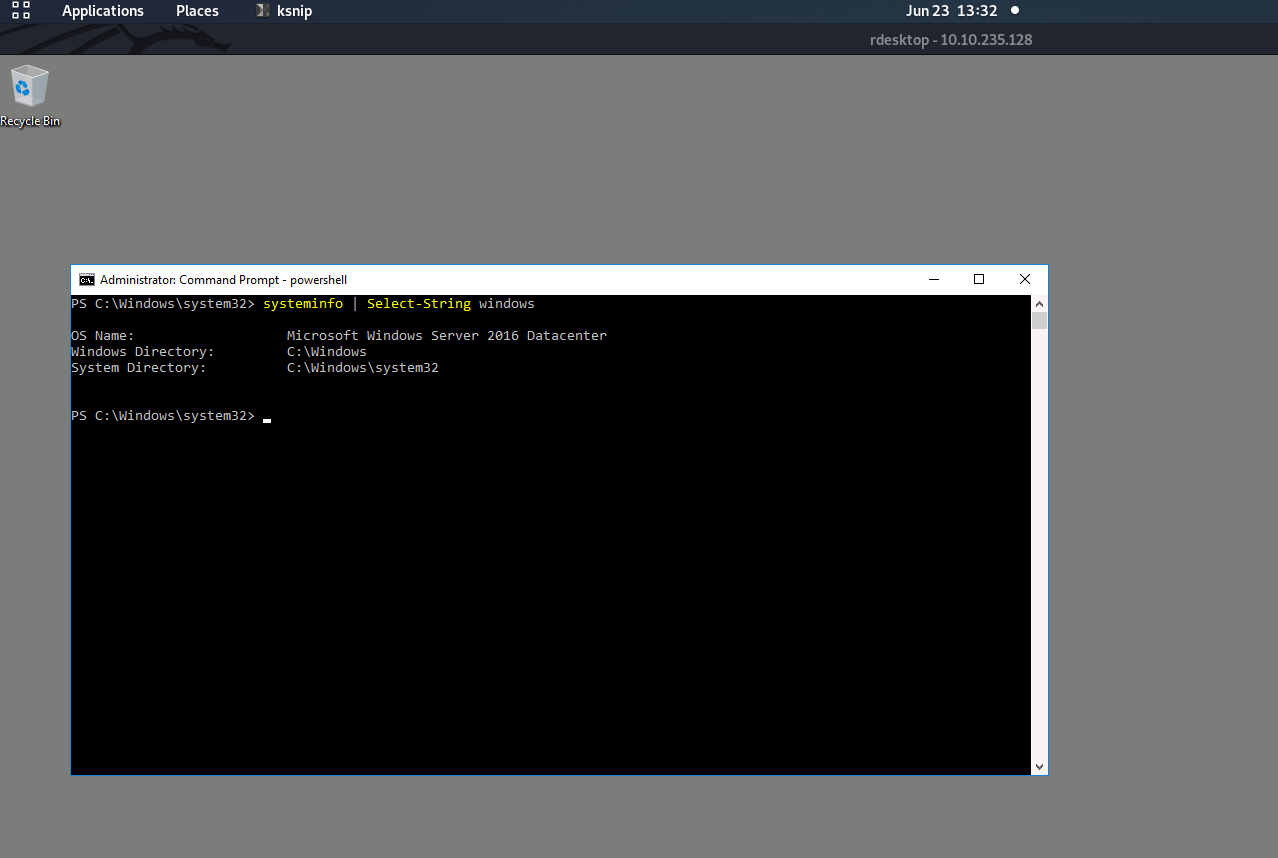
Qesution 1 : Whats the version and year of the windows machine ?
Correct Answer : Windows Server 2016
- So many ways to know about the OS info
I going to use Powershell Command and do pipe and grep same like Linux by use Select-String Module, to get the result easy way
system info | Select-String windows
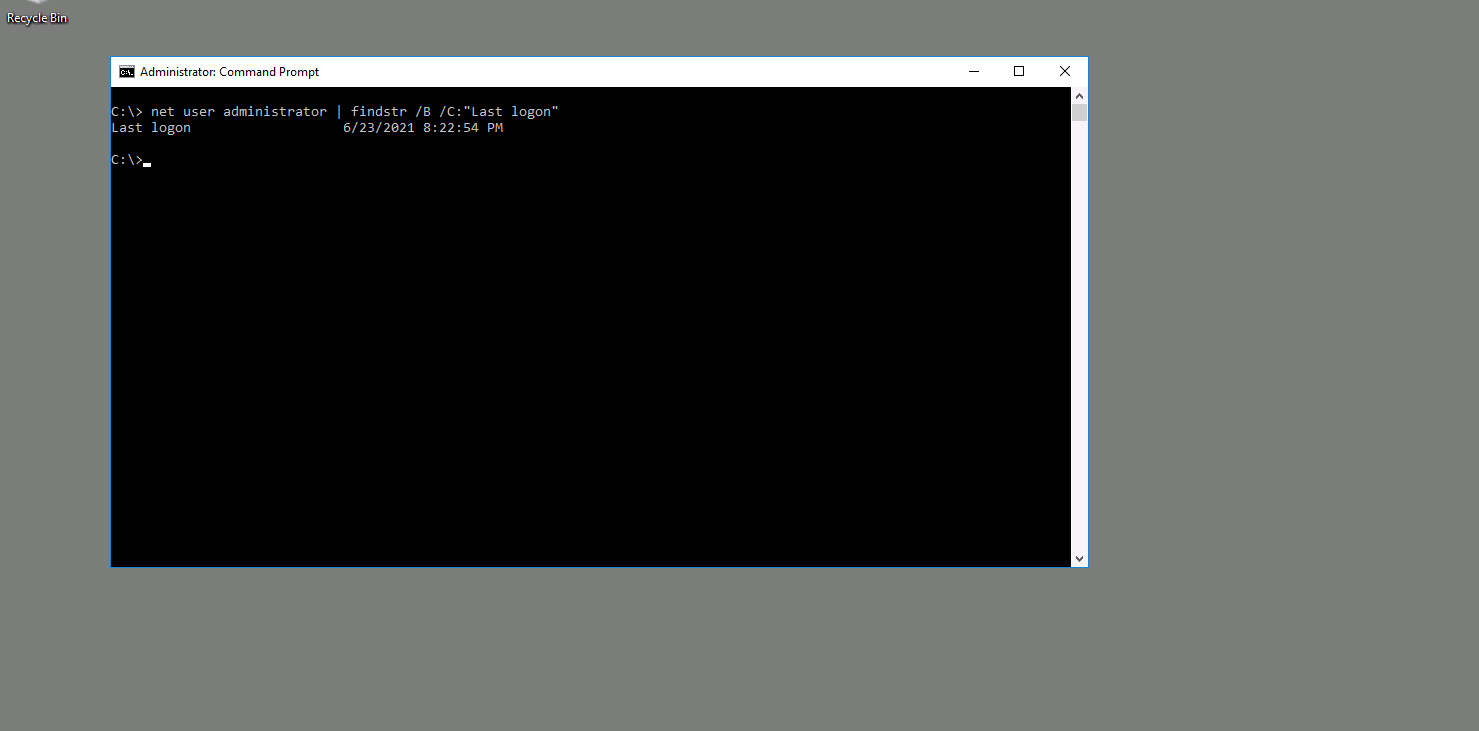
Qesution 2 : Which user logged in last ?
Correct Answer : Administrator
I am login as Administrtor so last login Administrator
net user administrator | findstr /B /C:"last logon"
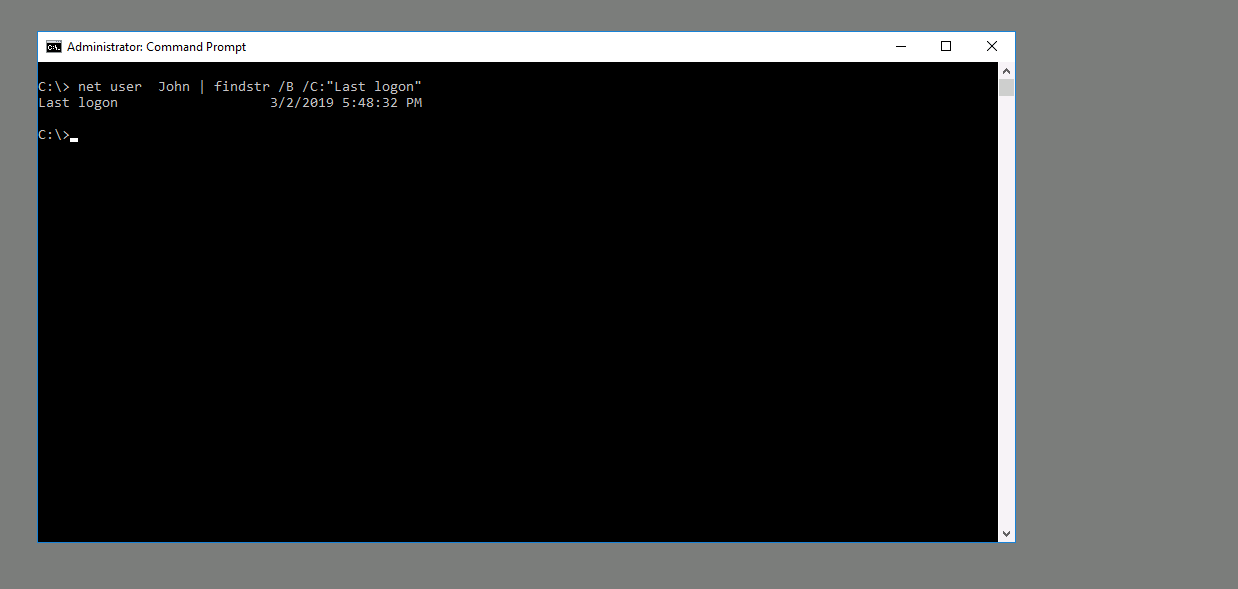
Qesution 3 : When did John log onto the system last? Answer format: MM/DD/YYYY H:MM:SS AM/PM
Correct Answer : 03/02/2019 5:48:32 PM
- I going to use same command but change the user name to john :
net user john | findstr /B /C:"last logon"
Qesution 4 : What IP does the system connect to when it first starts?
Correct Answer : 10.34.2.3
When the machine boots up, the IP address popup in the cmd window. another way the IP address store in the register key run
it makes the connection established every reboot
so,
I am going to check the register key
open cmd type regedit
navigate to the
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Qesution 5 : What two accounts had administrative privileges (other than the Administrator user)? Answer format: username1, username2
Correct Answer : Jenny, Guest
by Powershell, I use the module Get-LocalGroupName to allow me to list administrator group
Get-LocalGroupName -Name administrators
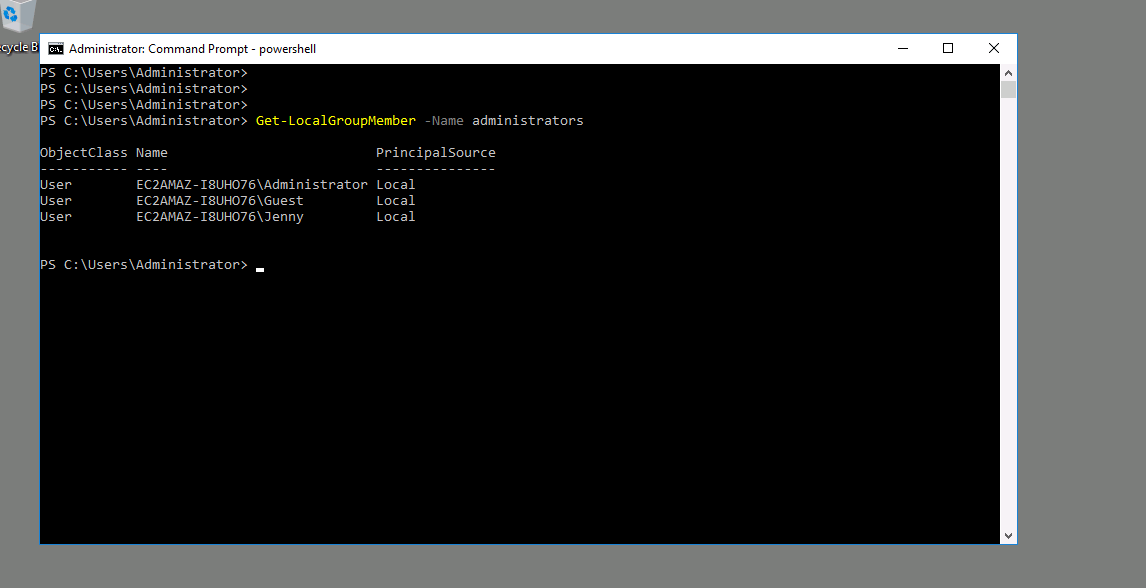
Qesution 6 : Whats the name of the scheduled task that is malicous.
Correct Answer : Clean file system
I will use
schtasks /query
to list all the tasks and direct the output to file call task.xml at desktop so I can read the tasks after checking all Tasks I found task call clean file system is malicious task if you Check the action for this Task you will find the PowerShell natcat script so this, not a Normal task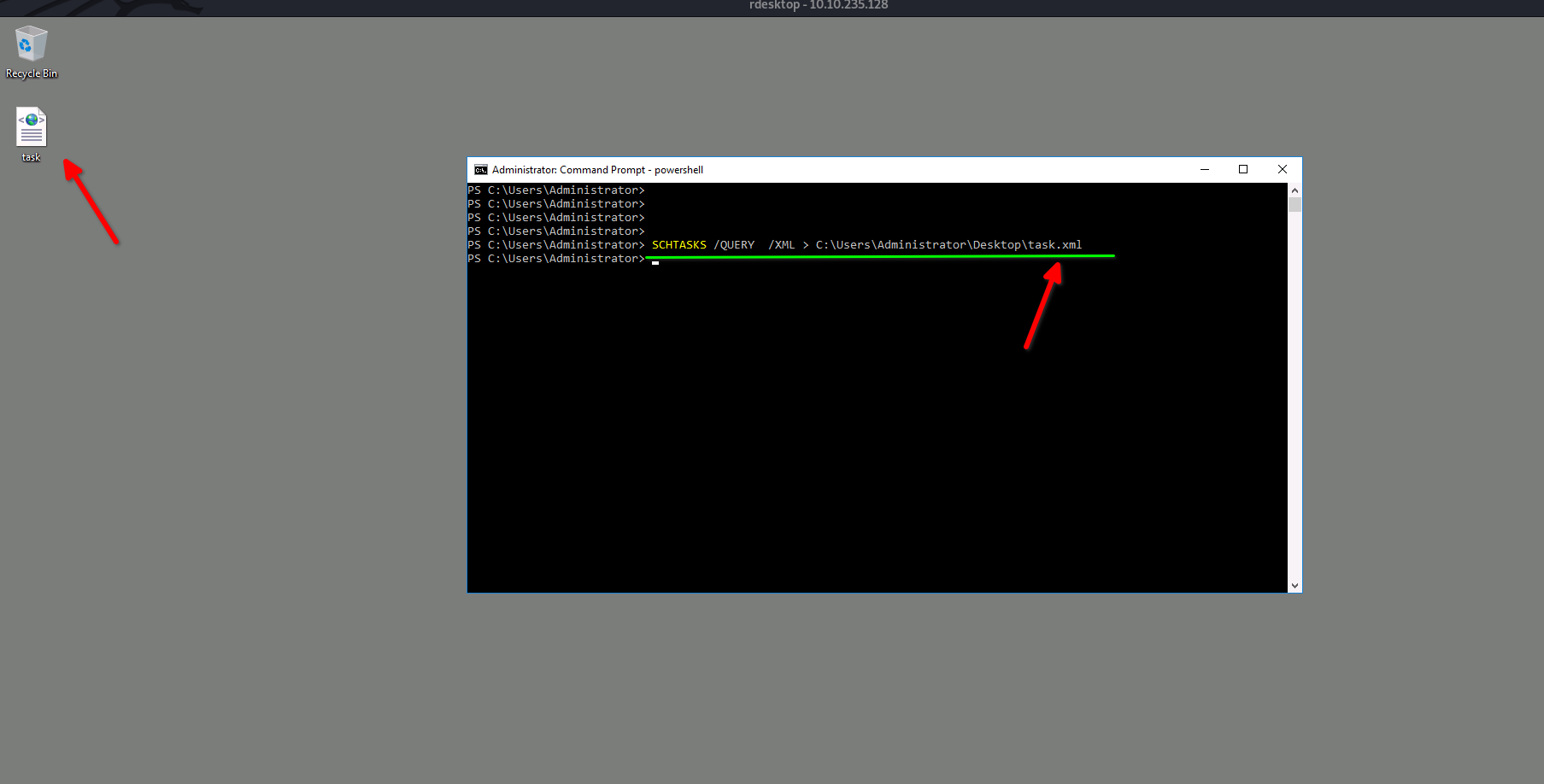
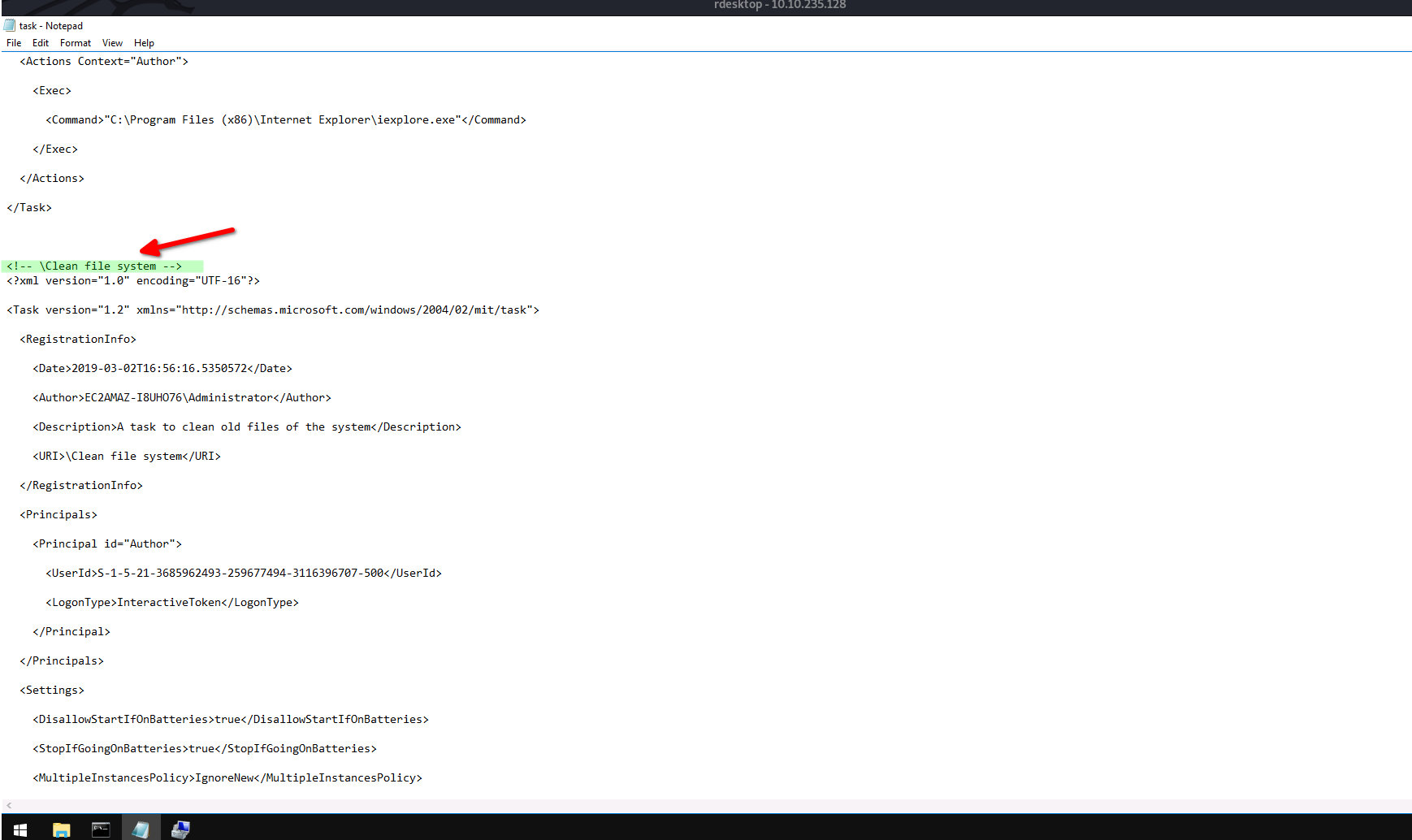
Qesution 7 : What file was the task trying to run daily?
Correct Answer : nc.ps1
as I read the action of this task, this task to run the NC PowerShell script file name nc.ps1

Qesution 8 : What port did this file listen locally for?
Correct Answer : 1348
Also, on the action Section, the port it found as an argument
so the Full command is nc.ps1 -l 1348
it means the netcat listener at this port for any coming connection

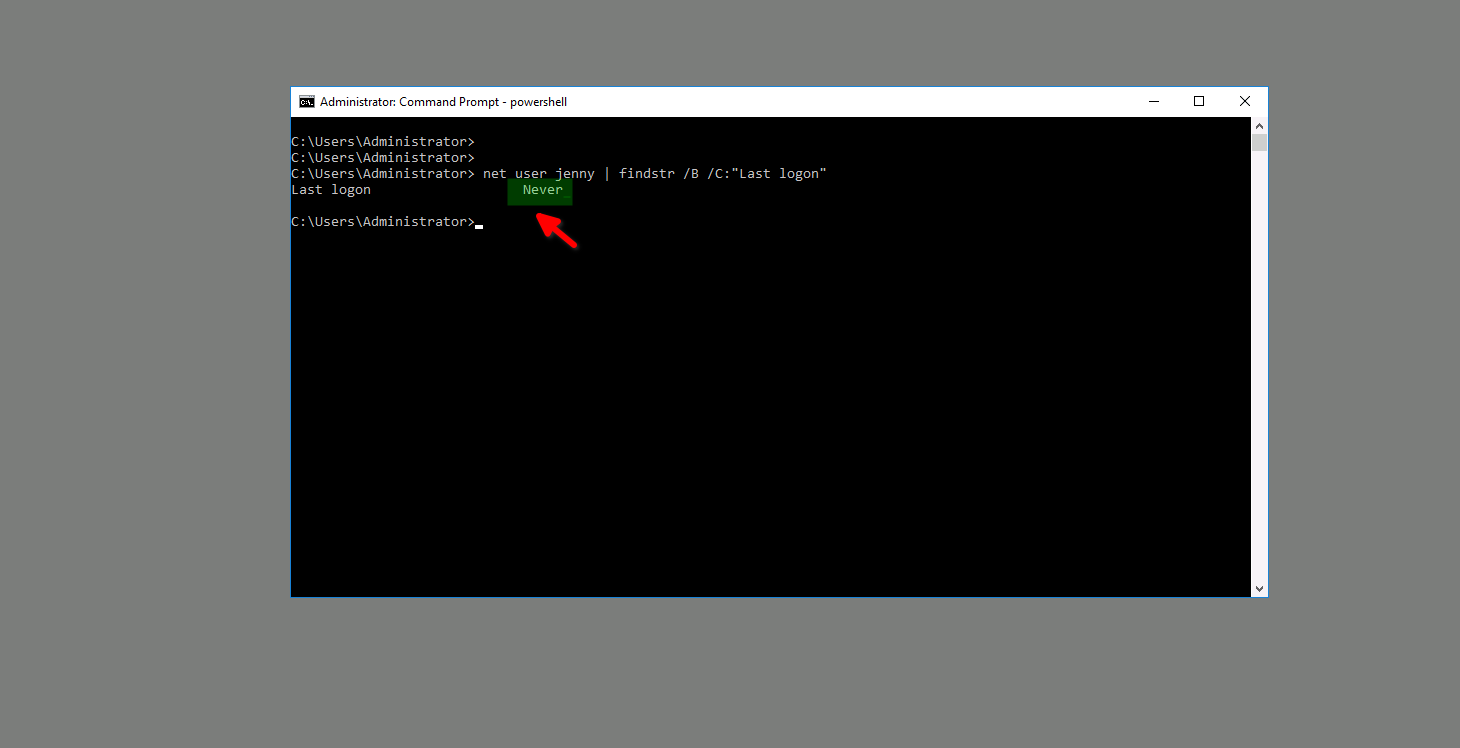
Qesution 9 : When did Jenny last logon?
Correct Answer : Never
I going to use same command but change the user name to Jenny :
net user Jenny | findstr /B /C:"last logon"
Qesution 10 : At what date did the compromise take place?
Correct Answer : 03/02/2019
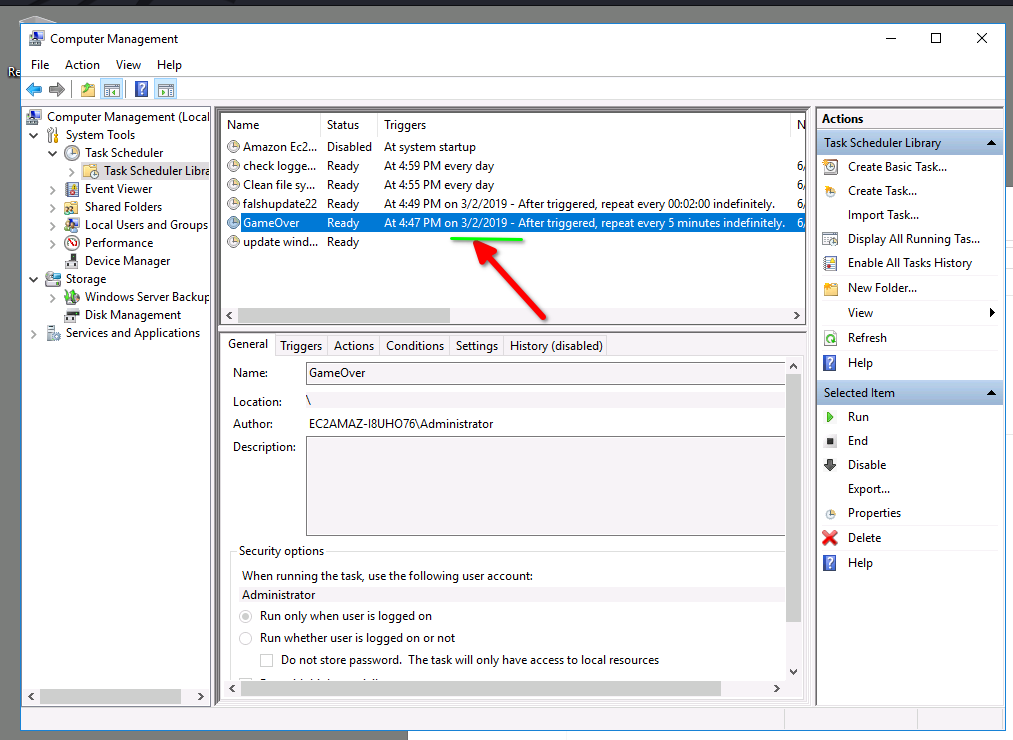
I going to open the computer management then I will open the task scheduled
so all Tasks are list by the time
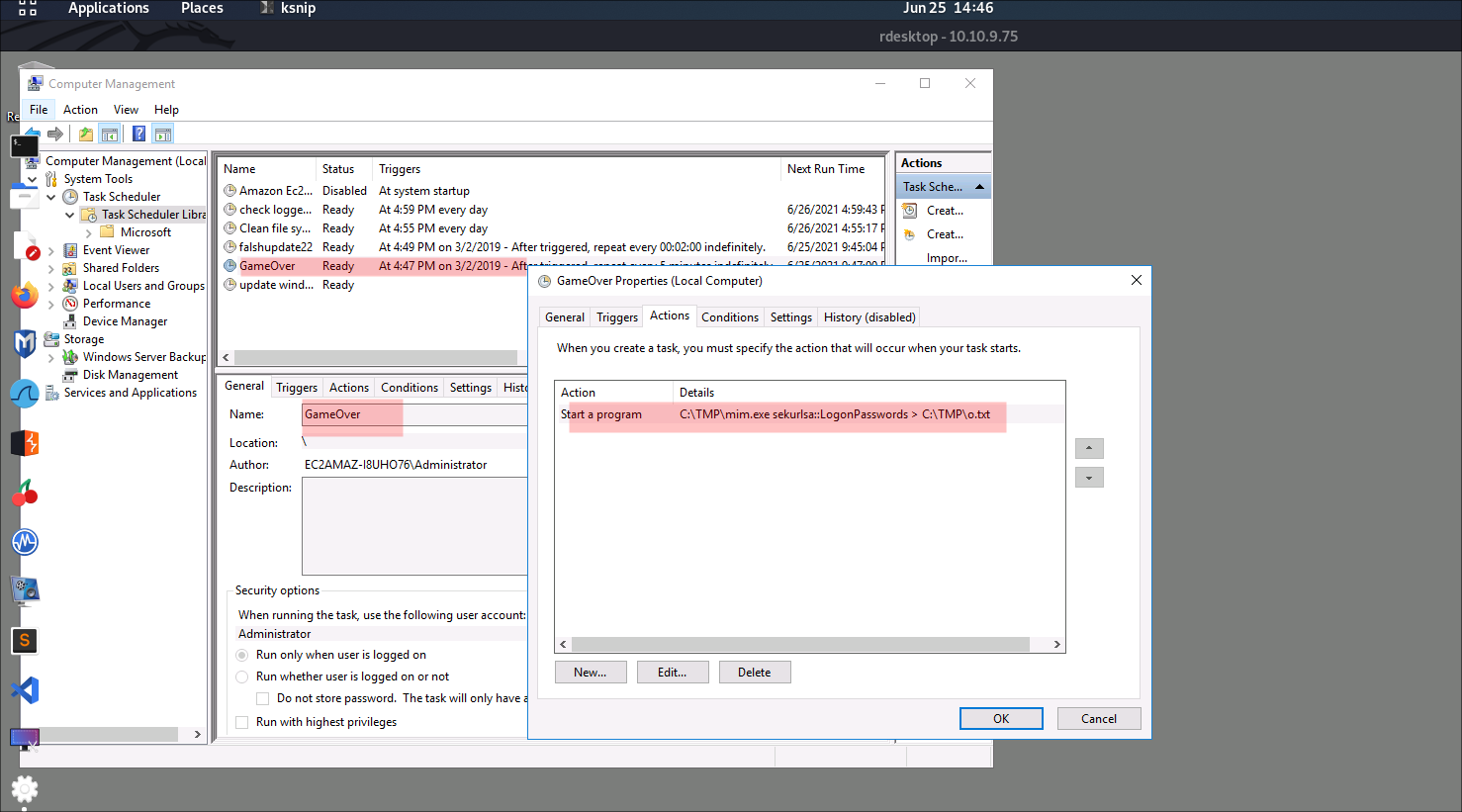
so GameOver task is the task run the first-time run on 03/02/2019, And it will run every 5 minutes
this task will call mim.exe to hashdump the password and add output to file at same dir, the first time run it this first time the machine get a compromise to take place
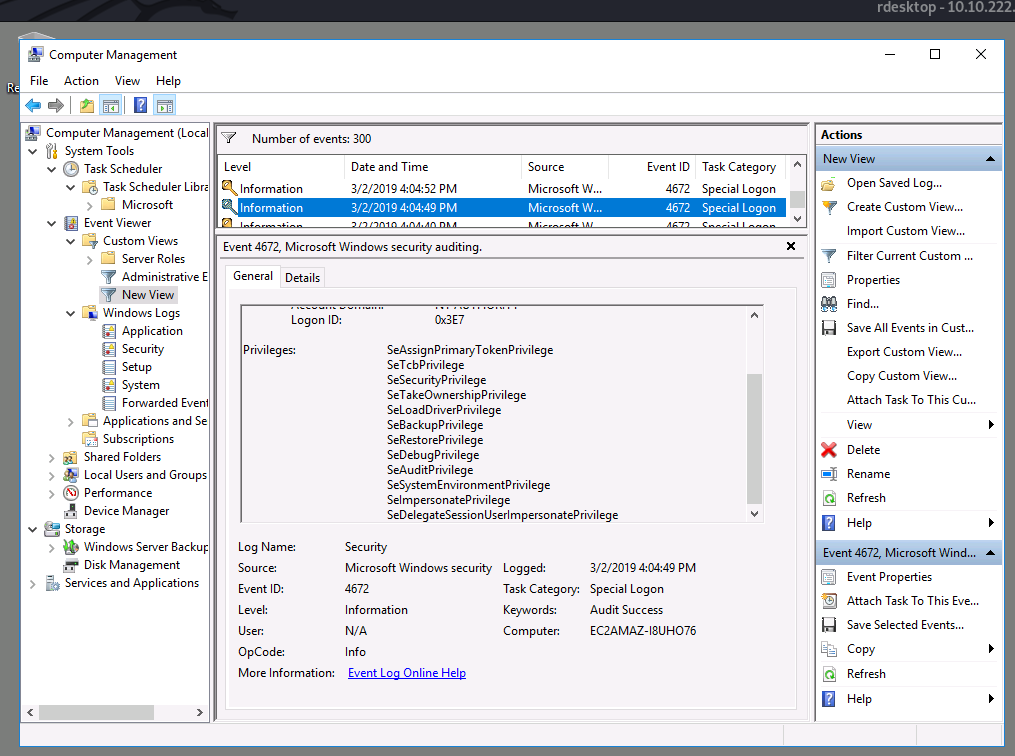
Qesution 11 : At what time did Windows first assign special privileges to a new logon? Answer format: MM/DD/YYYY HH:MM:SS AM/PM
Correct Answer : 03/02/2019 4:04:49 PM
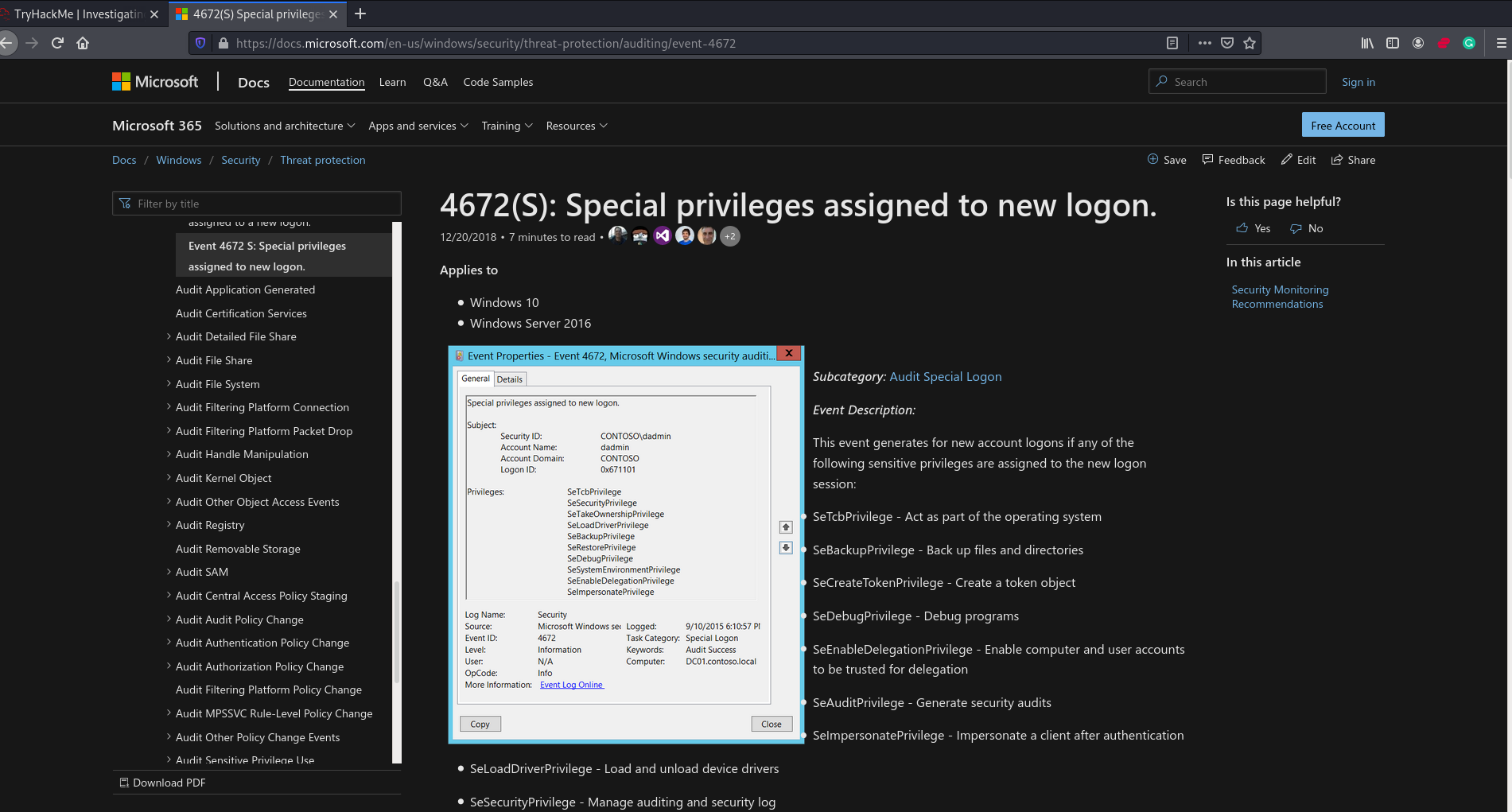
I am going to open Google then I search for a Specia privileges login id
so I found a Microsoft page explaining So the numeric id of the Special login is 4672
so I will filter all security logs, I saw so many task id 4672
use the hint is 00/00/0000 0:00:49 PM
so the answer is
03/02/2019 4:04:49 PM
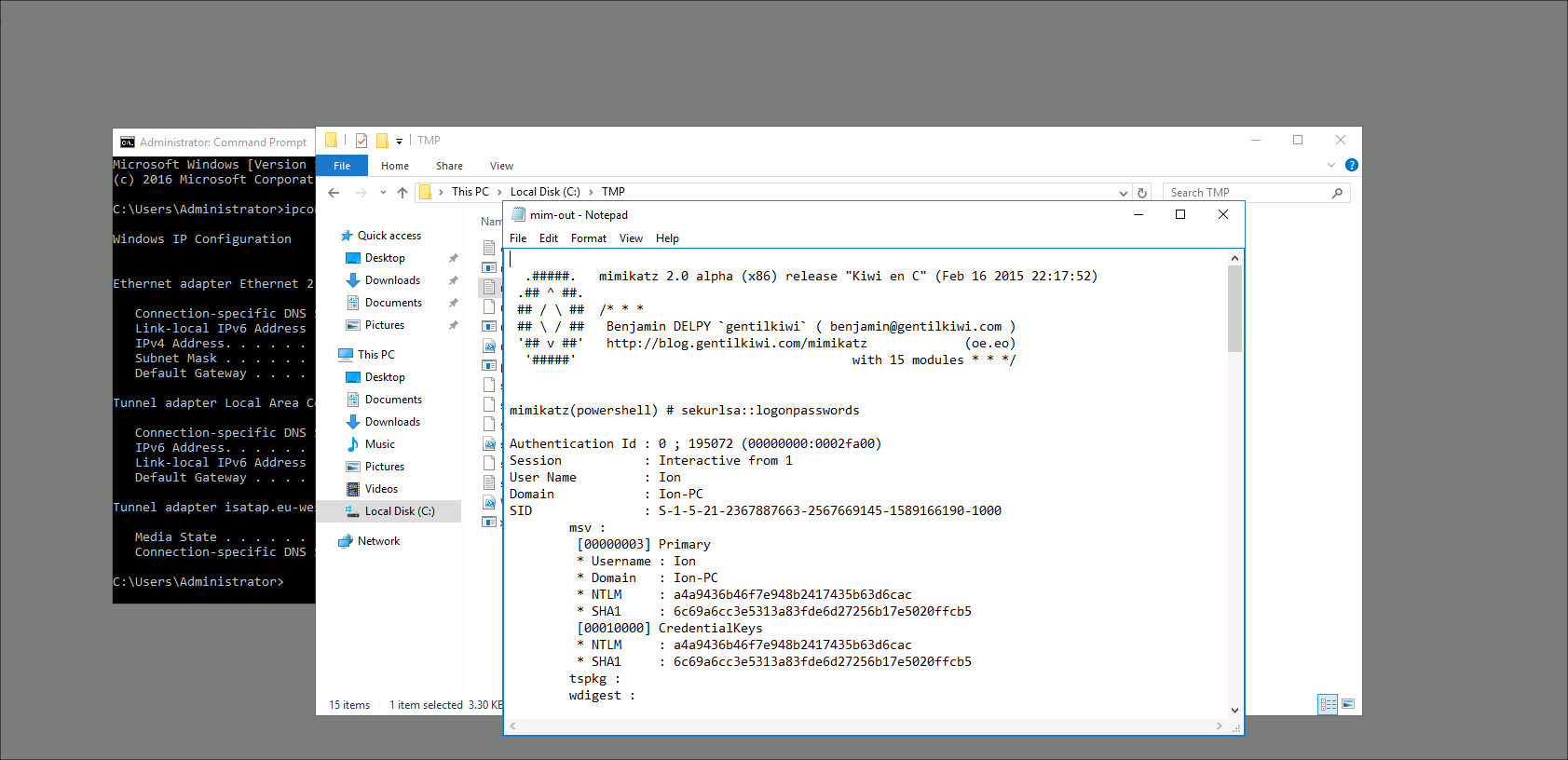
Qesution 12 : What tool was used to get Windows passwords?
Correct Answer : Mimikatz
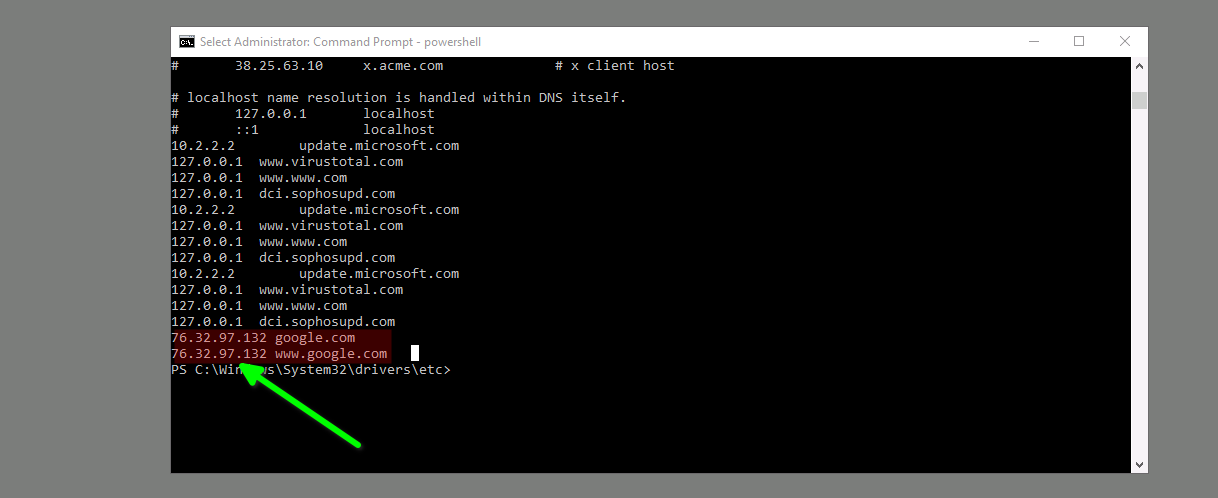
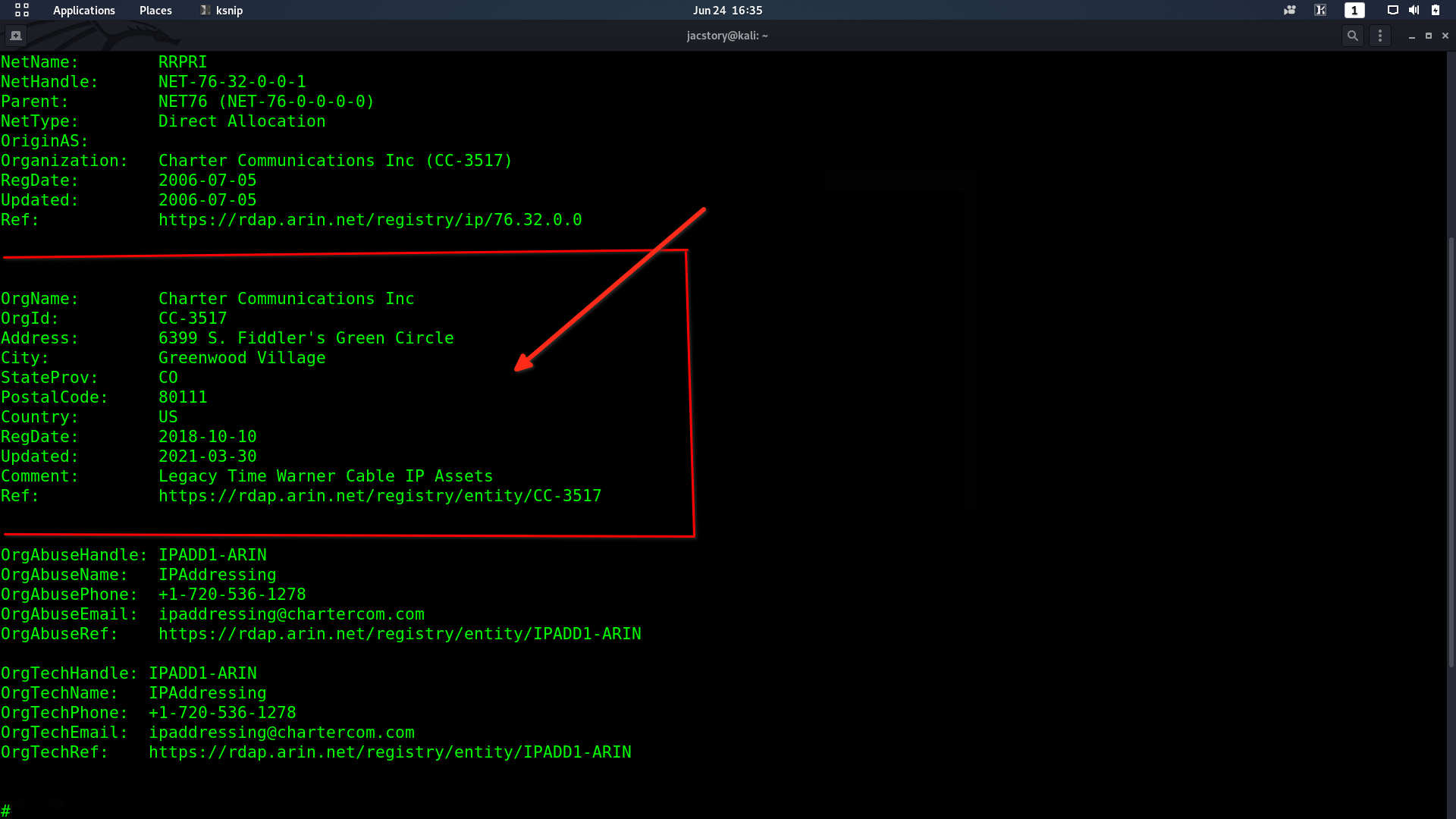
Qesution 13 : What was the attackers external control and command servers IP?
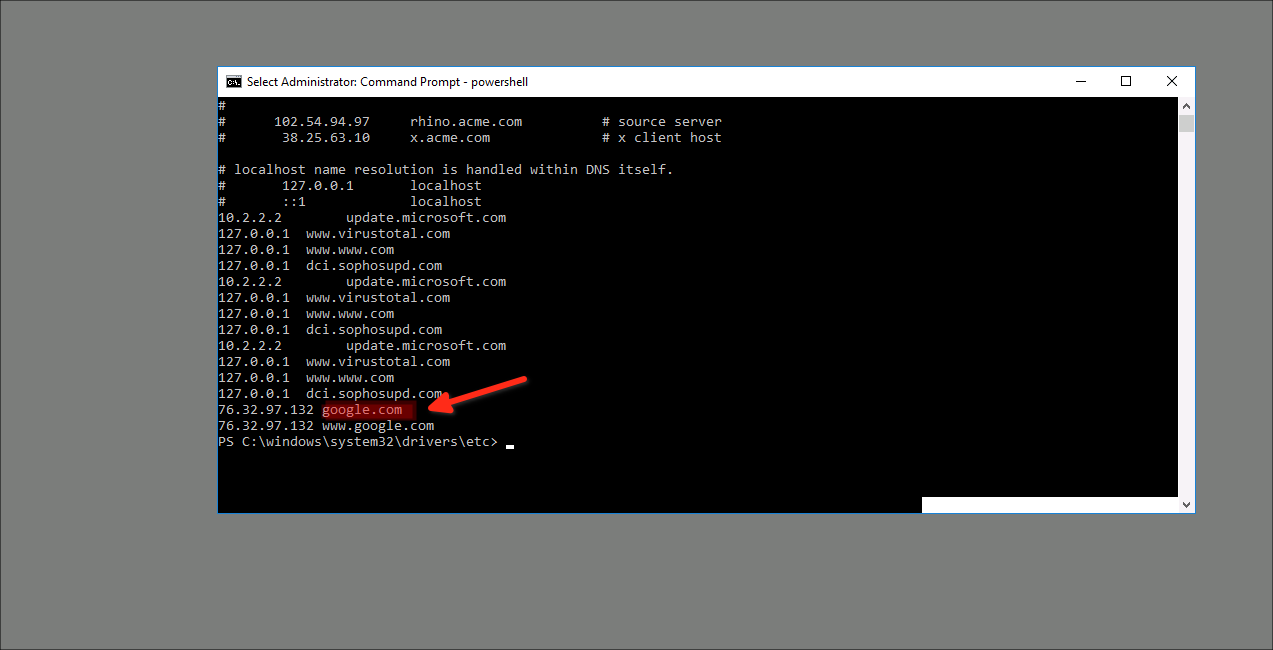
Correct Answer : 76.32.97.132
the host file has the IP address as First DNS, So I will cat host file to see what is the change on it so we have some changes on the host file, so 127.0.0.1 is the loopback localhost, and another IP added by hacker tool so he adds for google.com 76.32.97.132, so any time to go open google will go for this address, not a google IP to be suer open terminal and type whois 76.32.97.132 the result no google
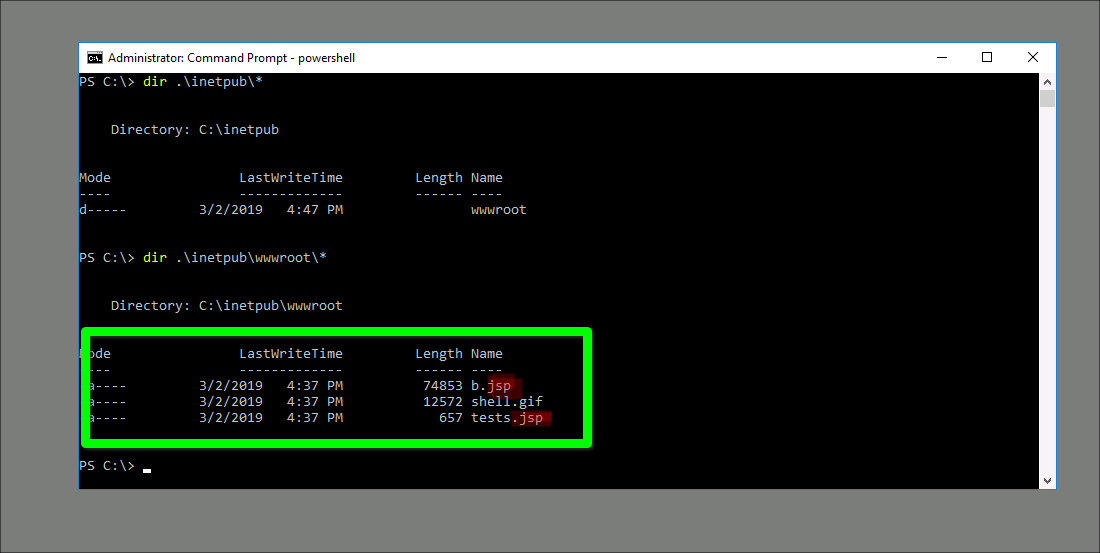
Qesution 14 : What was the extension name of the shell uploaded via the servers website?
Correct Answer : .jsp
check file inetpub\wwwroot by cat command the file extension .jsp
javascript
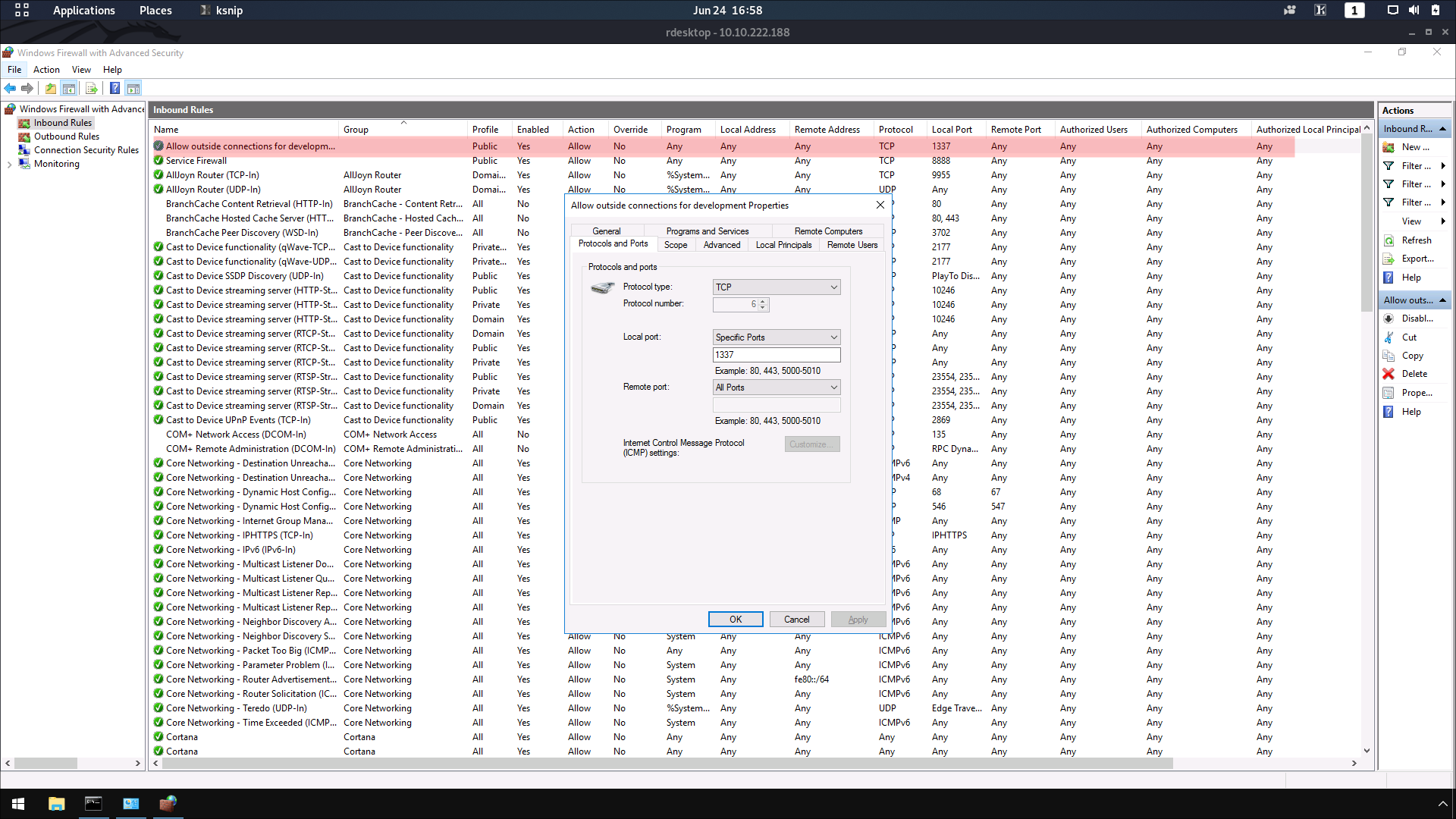
Qesution 15 : What was the last port the attacker opened?
Correct Answer : 1337
check the firewall for port allow incoming connection I found 1337 especial port
Qesution 16 : Check for DNS poisoning, what site was targeted?
Correct Answer : google.com
see the answer Qesution 13