Welcome To Linux Fundamentals Part3 ‘writeup’
-
by : Ahmedhammad
–info
- room name : LinuxFundamentalsPart3
- category : Linux Fundamental
- Welcome to part three (and the finale) of the Linux Fundamentals module. So far, throughout the series, you have got hands-on with some fundamental concepts and used some important commands. This room is going to showcase some useful utilities and applications that you are likely to use day-to-day. You’re also going to advance your Linux-fu skills by learning about automation, package management, and service/application logging.
Watch the video by tryhackme :
https://www.youtube.com/watch?v=bwgaZCb2ft8
Starting Point
task1 : Introduction
Qesution 1 : Let's proceed!
Correct Answer : No answer needed
Task 2 : Deploy Your Linux Machine
Qesution 1 : I've logged into the Linux Fundamentals Part 3 machine using SSH and have deployed the AttackBox successfully!
Correct Answer : No answer needed
## Task 3 : Terminal Text Editors
Qesution 1 : Create a file using Nano
Correct Answer : No answer needed
To Create file using nano
just type nano and the file name you want create
same like
nano tryhackme
Qesution 2 : Edit "task3" located in "tryhackme"'s home directory using Nano. What is the flag?
Correct Answer : THM{TEXT_EDITORS}
ls
nano task3
THM{TEXT_EDITORS}
Task 4 : General/Useful Utilities
Qesution 1 : Ensure you are connected to the deployed instance (10.10.79.225)
Correct Answer : No answer needed
Qesution 2 : Now, use Python 3's "HTTPServer" module to start a web server in the home directory of the "tryhackme" user on the deployed instance.
Correct Answer : No answer needed
Qesution 3 : Download the file http://10.10.79.225:8000/.flag.txt onto the TryHackMe AttackBox What are the contents?
Correct Answer :THM{WGET_WEBSERVER}
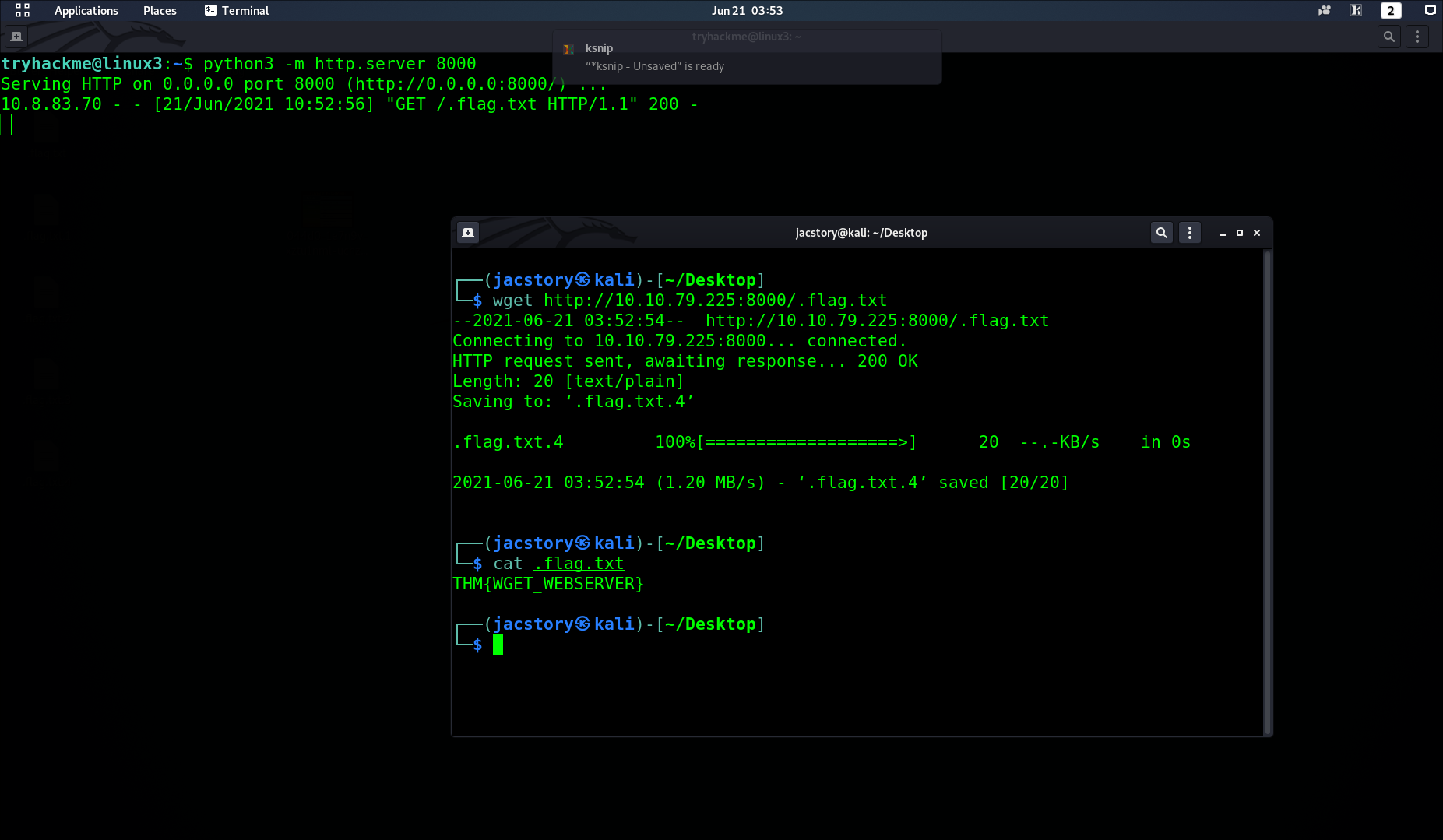
Qesution 4 : Create and download files to further apply your learning -- see how you can read the documentation on Python3's "HTTPServer"module. Use Ctrl + C to stop the Python3 HTTPServer module once you are finished. .
Correct Answer : No answer needed
Task 5 : Processes 101
Qesution 1 : Read me!
Correct Answer : No answer needed
Qesution 2 : If we were to launch a process where the previous ID was "300", what would the ID of this new process be?
Correct Answer : 301
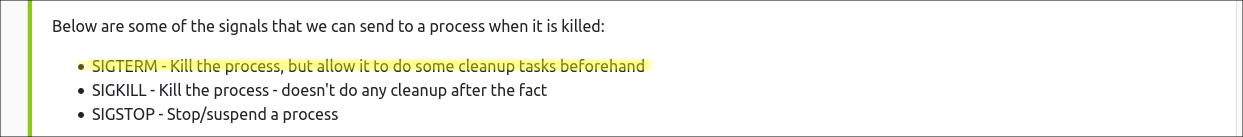
Qesution 3 : If we wanted to cleanly kill a process, what signal would we send it ?
Correct Answer : SIGTERM
SIGTERM - Kill the process, but allow it to do some cleanup tasks beforehand
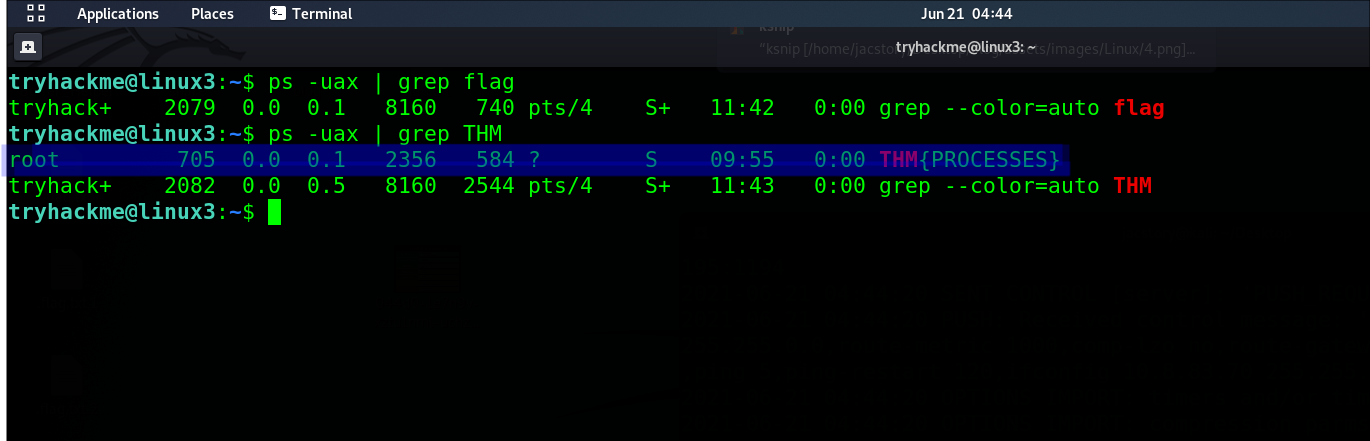
Qesution 4 : Locate the process that is running on the deployed instance (10.10.79.225). What flag is given?
Correct Answer : THM{PROCESSES}
ps -uax | grep THM
Qesution 5 : What command would we use to stop the service "myservice"?
Correct Answer : systemctl stop myservice
to stop service type systemcty stop ‘service name’
Qesution 6 : What command would we use to start the same service on the boot-up of the system?
Correct Answer : systemctl enable myservice
to enable service command is systemctl enable ‘service name’
Qesution 7 : What command would we use to bring a previously backgrounded process back to the foreground?
Correct Answer : fg
fg to make process in background
Task 6 : Maintaining Your System: Automation
Qesution 1 : Ensure you are connected to the deployed instance and look at the running crontabs.
Correct Answer : No answer needed
Qesution 2 : What command would we use to bring a previously backgrounded process back to the foreground?
Correct Answer : @reboot
@reboot command allowed to use command every reboot the machine same like
@reboot macchanger -r wlan0
this command make you change your mac address every reboot
Task 7 : Maintaining Your System: Package Management
Qesution 2 : Since TryHackMe instances do not have an internet connection...this task only requires you to read through the material.
Correct Answer : No answer needed
Task 8 : Maintaining Your System: Logs
Qesution 1 : Look for the apache2 logs on the deployable Linux machine
Correct Answer : No answer needed
Qesution 2 : What is the IP address of the user who visited the site?
Correct Answer : 10.9.232.111
cd /var/log/apache2/
cat access.log.1
