Welcome To the Encryption crypto tryhackme room ‘writeup’
-
by : Ahmedhammad
–info
- room name : Encryption-Crypto101
- category : Crypto
- link : https://www.tryhackme.com/room/encryptioncrypto101
This room will cover:
- Why cryptography matters for security and CTFs
- The two main classes of cryptography and their uses
- RSA, and some of the uses of RSA
- 2 methods of Key Exchange
Starting Point
task1
Qesution 1 : I'm ready to learn about encryption ?
Correct Answer : No answer needed
task2
Qesution 2 : I agree not to complain too much about how theory heavy this room is ?
Correct Answer : No answer needed
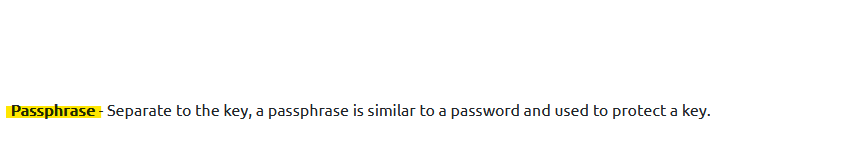
Qesution 3 : Are SSH keys protected with a passphrase or a password ?
Correct Answer : passphrase
task3
Qesution 4 : What does SSH stand for? ?
Correct Answer : Secure Shell
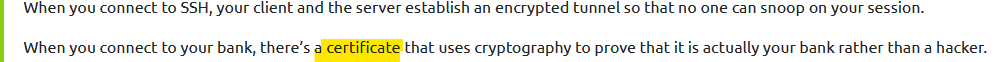
Qesution 5 :How do webservers prove their identity ?
Correct Answer : certificates
Qesution 6 : What is the main set of standards you need to comply with if you store or process payment card details ?
Correct Answer : PCI-DSS

task4
Qesution 7 : What's 30 % 5 ?
Correct Answer : 0
Qesution 8 : What's 25 % 7 ?
Correct Answer : 4
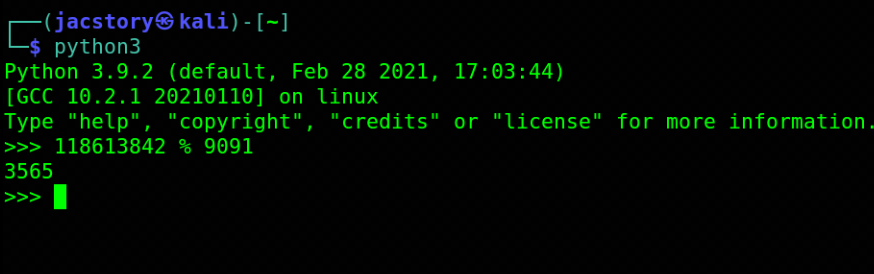
Qesution 9 : What's 118613842 % 9091 ?
Correct Answer : 3565
will use python as the Hint
task5
Qesution 10 : Should you trust DES? Yea/Nay ?
Correct Answer : Nay
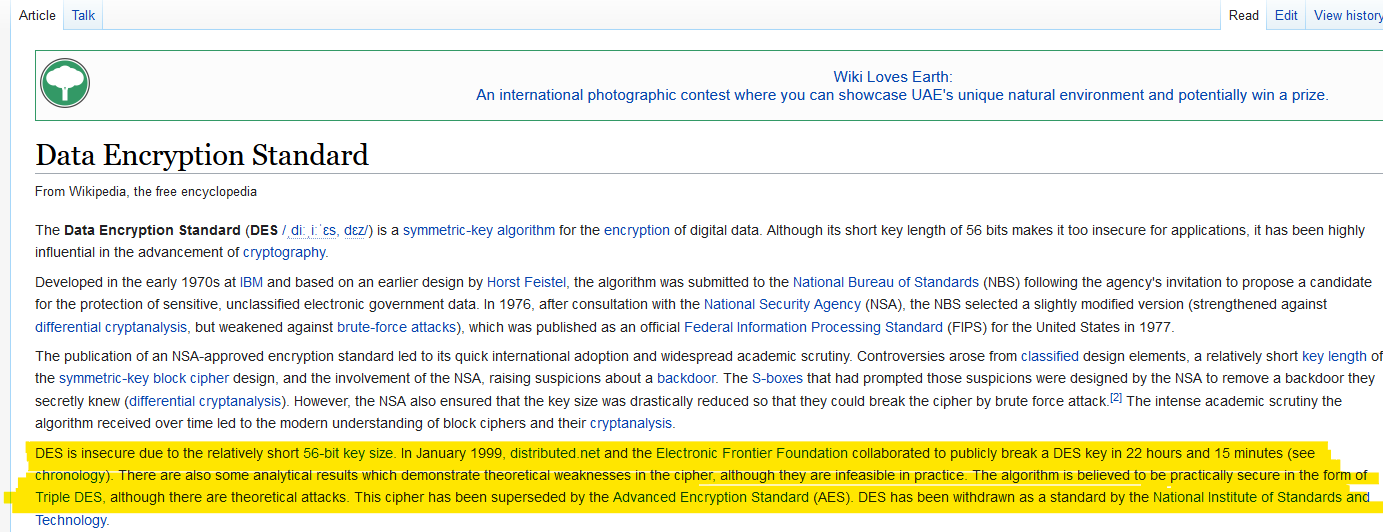
Qesution 11 : What was the result of the attempt to make DES more secure so that it could be used for longer ?
Correct Answer : Triple DES
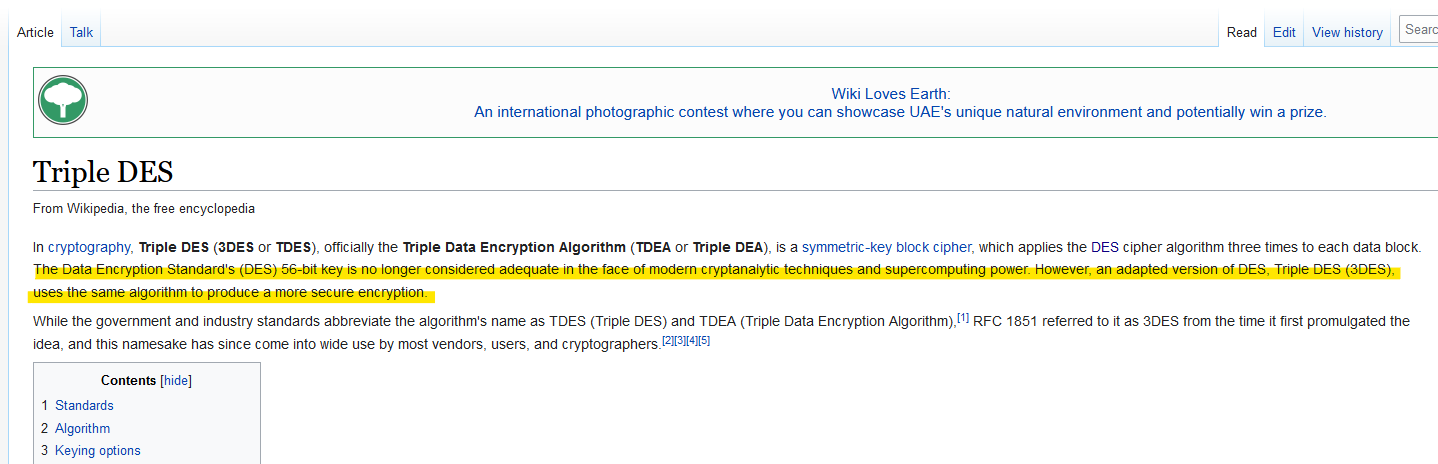
Qesution 12 : Is it ok to share your public key? Yea/Nay ?
Correct Answer : Yea
you only need to share public key and private key shoud kept as private

task6
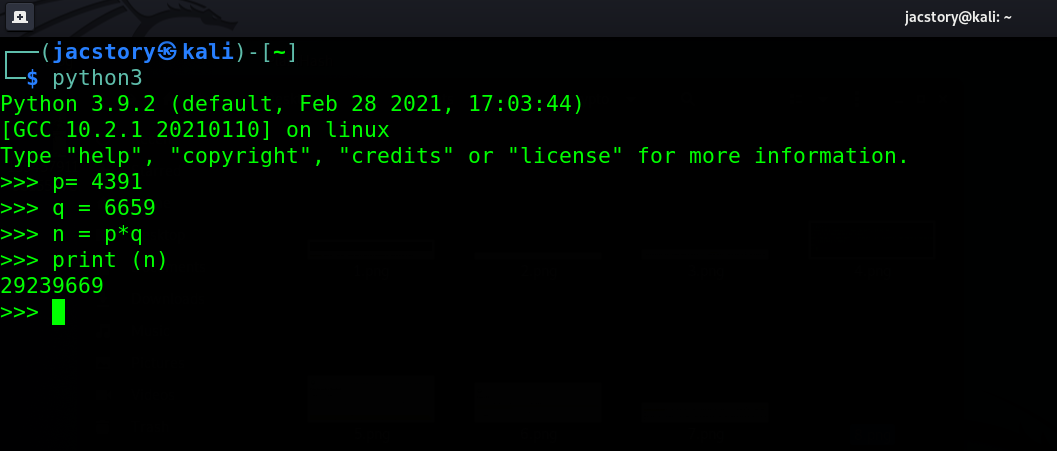
Qesution 13 : p = 4391, q = 6659. What is n ?
Correct Answer : 29239669
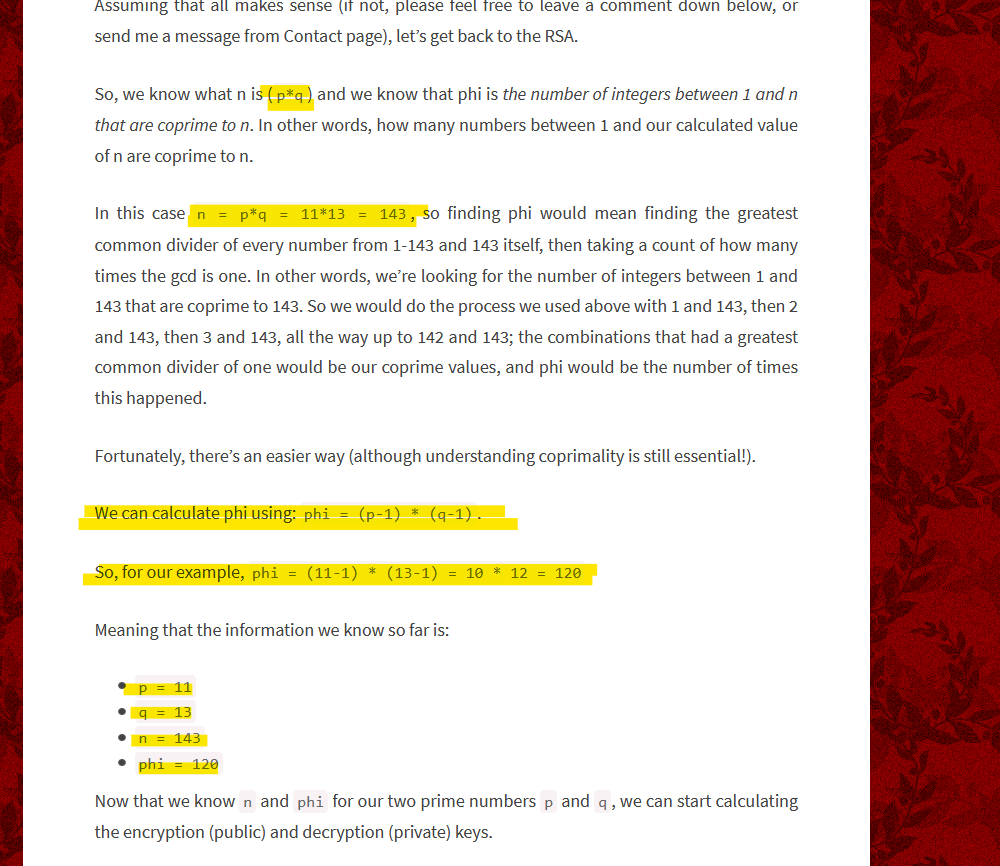
as we can see if you know p and q so n = p*q so i will gonna use pyhton to calculated
Qesution 14 : understand enough about RSA to move on, and I know where to look to learn more if I want to.
Correct Answer : no answer needed
task7
Qesution 15 : I understand how keys can be established using Public Key (asymmetric) cryptography .
Correct Answer : no answer needed
task 8
Qesution 16 : I understand how keys can be established using Public Key (asymmetric) cryptography .
Correct Answer : CloudFlare
task9
Qesution 17: I recommend giving this a go yourself. Deploy a VM, like Linux Fundamentals 2 and try to add an SSH key and log in with private key.
Correct Answer : no answer needed
Qesution 18 : Download the SSH Private Key attached to this room.
Correct Answer : no answer needed
Qesution 19 : What algorithm does the key use ?
Correct Answer : rsa
the answer is the file name you downloaded ‘idrsa.id_rsa’ as we know about the algoritm ssh use is ‘ Rivest–Shamir–Adleman ‘ cryptosystem
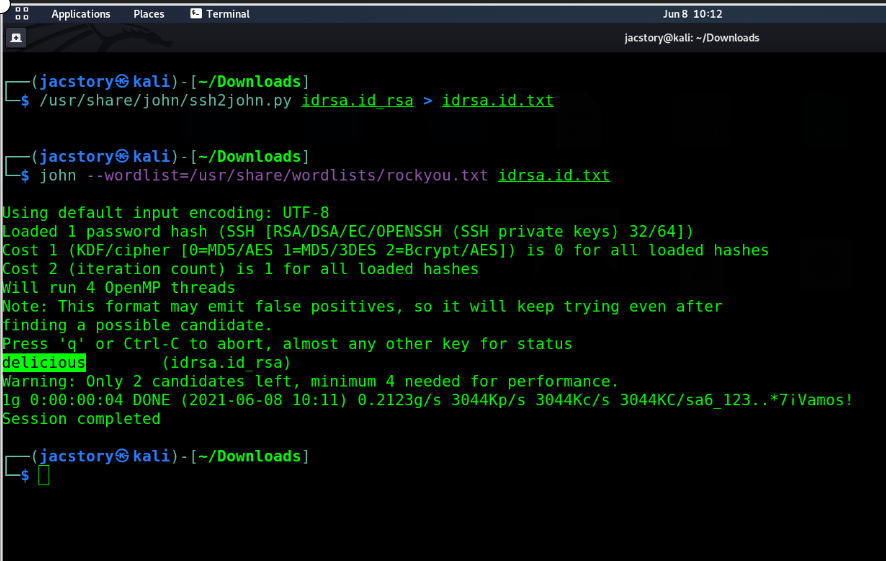
Qesution 20 : Crack the password with John The Ripper and rockyou, what's the passphrase for the key ?
Correct Answer : delicious
first of all to crack the password from the ras file we need to use ssh2jonh.py
this tools come with john the Ripper the path is /usr/share/jonh/ssh2jonh.py
the command
/usr/share/john/ssh2john.py idrsa.id_rsa > idrsa.id.txt
redirect output to file.txt
then use john the Ripper to crack the password in side the file txt
john –wordlist=/usr/share/wordlists/rockyou.txt idrsa.id.txt
the password is : delicious
task 10
Qesution 21 : I understand how Diffie Hellman Key Exchange works at a basic level.
Correct Answer : no answer needed
task 11
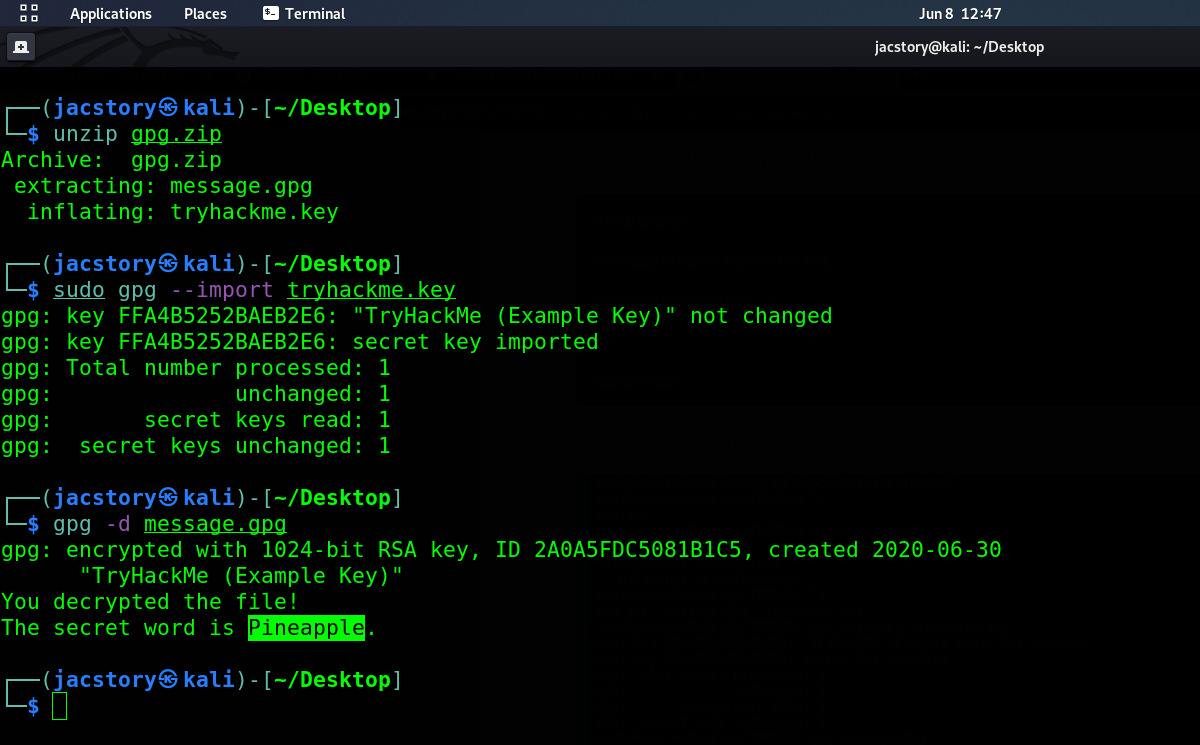
Qesution 22 : Time to try some GPG. Download the archive attached and extract it somewhere sensible.
Correct Answer : no answer needed
Qesution 23 : You have the private key, and a file encrypted with the public key. Decrypt the file. What's the secret word ?
Correct Answer : Pineapple
- unzip the file use unzip gpg.zip
- now we have the key and the message
- the tryhackme.key
- message is message.gpg
- try to import the key by using
- sudo gpg –import tryhackme.key
- use gpg -d message.gpg
- The secret word is Pineapple